OpenSRS offers an impressive lineup of SSL certificate products.
We’ve received a few queries about Subject Alternative Name (SAN) certificates and how they differ from wildcard certs. With that in mind, we’ve put together a quick reference guide here.
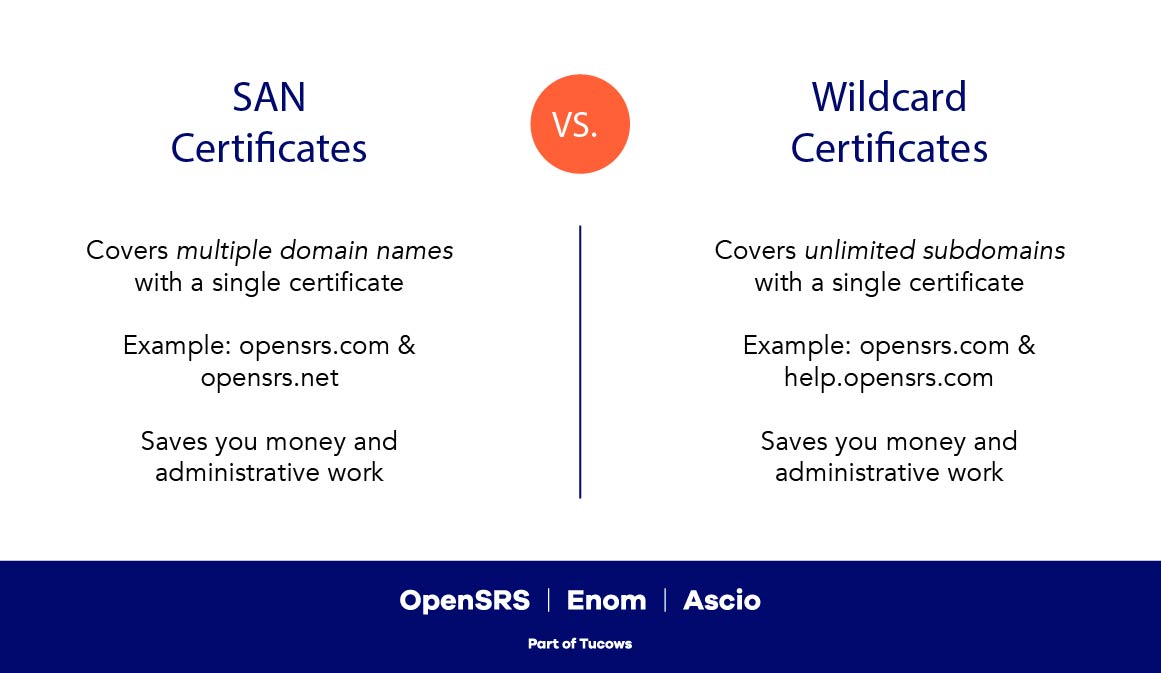
Let’s start with a basic look at both wildcard and SAN certs.
What is a SAN Certificate?
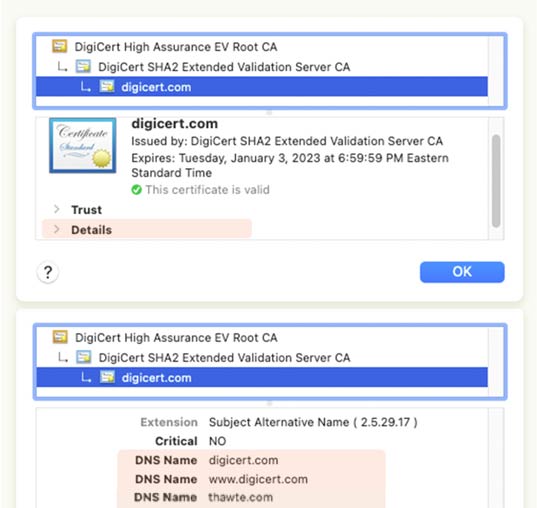
SAN certificates allow for multiple fully qualified domain names to be protected using a single certificate.
For example, you could get a certificate for the primary domain, opensrs.com, and then add more SAN values to have the same certificate protect opensrs.org, opensrs.net, and even tucows.com.
What is a Wildcard Certificate?
A wildcard SSL certificate, on the other hand, allows for unlimited subdomains to be protected with a single certificate.
For example, you could use a wildcard certificate for the primary domain name, opensrs.com, and that cert would also work for mail.opensrs.com, ftp.opensrs.com, and any other subdomain. The wildcard refers to the fact that the cert is provisioned for *.opensrs.com.
Here’s a handy graphic that summarizes the difference:
When to choose a wildcard and when to choose a SAN certificate
Wildcard certs are great for protecting multiple subdomains on a single domain. In many cases, the wildcard cert makes more sense than a SAN because it allows for unlimited subdomains and you don’t need to define them at the time of purchase. You could provision *.opensrs.com and if at anytime during the life of the certificate, you decided to add www3.opensrs.com or mail.opensrs.com, that certificate would automatically protect these subdomains, no reissue required.
If, on the other hand, you need to protect multiple domain names, then the SAN certificate might be the right choice. For example, if you wanted to protect opensrs.com and opensrs.net. One caveat – you need to define the additional domains and add them to the certificate (reissue required) for it to work. We’ve got a knowledge base article, How to add SAN(s) to an existing SSL certificate, that walks you through this process.
SAN certificates, like wildcard certs, are a great way to save some money and also to make administration a bit easier, as you can reduce the number of certificates provisioned since they cover multiple domains.
Some important things to note:
Most of the SSL certificates we sell that support SANs allow you to cover up to 250 domain names (including the primary domain name), and you simply pay a fee for each additional domain name you add. In most cases, the SAN values can be changed at any time during the life of the certificate – you just need to change the value, and then do a free re-issue.
Further questions? Just ask!
We hope that helps a bit in terms of understanding the applications for both SAN certificates and wildcard certs. We’ve answered a lot of common questions about SSL certificates, including the different levels of authentication they provide, (DV, OV, and EV SSL certificates), on our blog. If you need further help, we encourage you to contact our support team.
