When people think about SSL certificates, they’ll usually consider them useful for protecting certain aspects of a website, such as the checkout section when buying something online, or perhaps on a larger scale, online banking or webmail. Having a non-secure page for general content and then directing visitors to a secure page when they need to pass along private or confidential data has been considered the norm for many years. However, one has to wonder why offer any non-secure content at all?
Dial-up is long gone
Back in the days of dial-up access, bandwidth was a premium. Establishing a secure connection increases the amount of data between a webserver and a browser since the content being sent to a user’s browser is encrypted, so this would slow things down on an already slow connection. As technology has advanced, so has the speed of our internet connections, and the speed of the computers and servers that use it. Encryption is no longer the bottleneck it used to be, and thankfully so, because along with these advances in technology, there have also been advances in the threats by those with malicious agendas.
I’ve got nothing to hide
Privacy and security have made headlines in recent years, ranging from the vulnerabilities found in encryption software used by most computers and servers, to entities or individuals snooping on the traffic that is sent from one machine to another. Browsers have been touting their “private browsing” options that don’t retain any browsing history or cookies, and many people use these options on a daily basis, but even if your browsing habits are not stored locally, the traffic between a user’s computer and a non-secure website can still be monitored, or even hijacked.
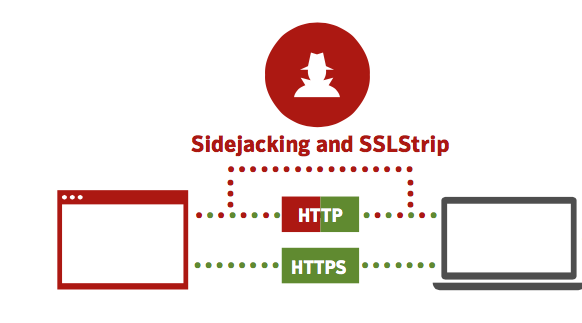
Time to batten down the hatches
This is where the concept of Always-On SSL comes into play, and it’s not as daunting as it sounds, nor is it difficult to implement. The basic concept is this: Any content that your webserver provides to any visitor should be done so via HTTPS. This means that any images or links back to other pages on your webserver should be using “https://” instead of “http://”. Your webserver should also be set to redirect any HTTP traffic immediately to HTTPS, so that visitors start with a secure connection, and stay there. This will mitigate the effectiveness of snooping or hijacking attacks.
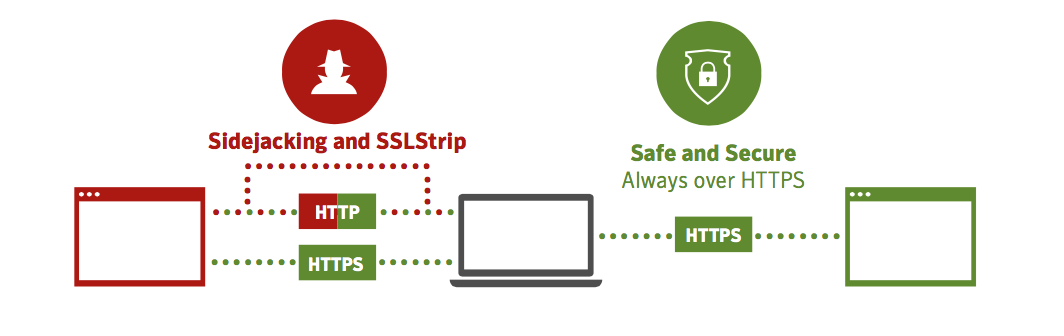
Only as strong as the weakest link
Ensuring that the content of the website is sent over HTTPS is one thing, yet the configuration of the webserver is another. People will often only concern themselves with the strength of the SSL certificate, such as using 2048-bit and SHA2, but that won’t be effective if the webserver uses outdated cryptology. Think of it like this: If you install a steel door at the front of your house, yet hold it in place with duct tape instead of bolting it, then it can’t be considered a secure door. It is imperative that webserver administrators follow the best practices for deploying SSL/TLS on their servers.
“What’s in it for me?”, you ask
Security is always going to be a primary concern for not only users of the Internet, but to those who maintain the servers that handle the available content. As an OpenSRS Reseller, SSL certificates offer large margins. They are also a natural complement to hosting packages, website builders and domain names. By introducing your customers to the concept of Always-On SSL, you can increase your margins and also help make the Internet a safer place.
Take a look at our impressive SSL offering >
Download Symantec’s quick reference guide to Always-On SSL >
