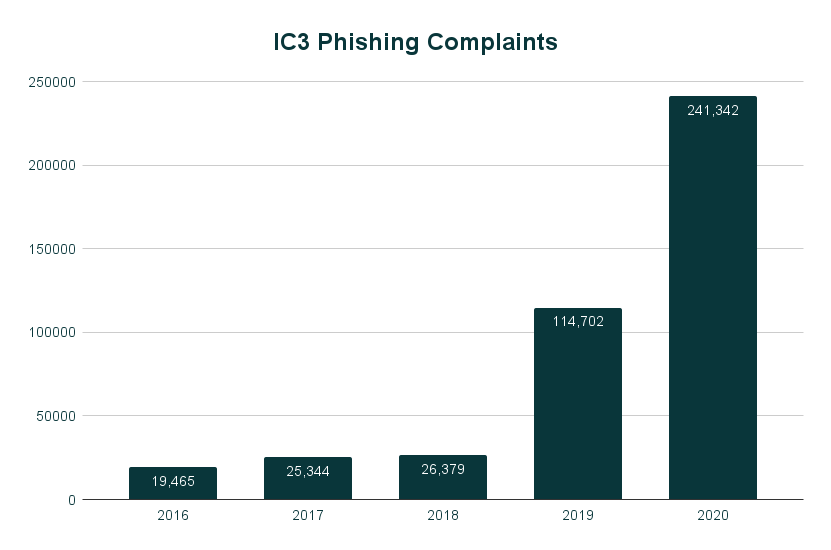
In 2021, cybercriminals delivered a tsunami of cyberattacks. PhishLabs reported a 47% increase in phishing attempts from Q1 2020 to Q1 2021. Another report by Cisco Umbrella revealed that of the organizations they surveyed, an astounding 86% had at least one employee try to connect to a phishing site. Phishing, and all its variations, continues to be popular with bad actors, accounting for 90% of data breaches.
Phishing attacks can target anyone. In November 2021, cybercriminals stole two million customer email addresses from US trading platform, Robinhood Markets, by successfully phishing a customer support employee. Even though Robinhood stated that no financial information was obtained, Robinhood customers will most likely be the target of follow-up phishing attacks that attempt to get their sensitive information.
What are phishing attacks?
Phishing is a cybercrime where someone sends an email, phone, or text message impersonating a reputable company, such as a bank, the IRS, or a store, to trick someone into disclosing sensitive personal data, such as credit card numbers, social security numbers, banking numbers, and passwords. In the message, they might explicitly ask for your account information or credentials, prompt you to download a document or app, or take you to a website where they then install malicious software on your computer or ask you to enter your data.
Protect yourself against phishing
While you can’t always immediately tell if an email or text is phishing, you can minimize the risk of becoming prey to phishing attacks (and help your customer do so too) by following a few best practices.
- Do not open suspicious, unsolicited messages, even those with enticing subject lines. Simply delete the message.
- Examine the email content. The email might include the company logo and even have the same layout as a legitimate email. Watch for grammatical errors, typos, and awkward language that may indicate that the email or text is not legitimate. However, instances of spelling and grammar mistakes are decreasing in phishing emails, as bad actors become increasingly sophisticated in their efforts to pose as a reputable company.
- Upgrade your OS and browsers often. Most browsers now come with anti-phishing filters.
- Avoid sites that are not secure. Most browsers display a “Not secure” warning when a site does not have the HTTPS security protocol enabled. HTTPS uses the TLS/SSL protocol to provide an encrypted and authenticated connection. HTTPS requires that you obtain and install a TLS/SSL certificate on your web server. This certificate can demonstrate that the organization that owns the certificate has been authenticated by a Certificate Authority. If your site doesn’t have HTTPS enabled, see this guide on how to choose the right TLS/SSL certificate.
- Do not click on a link unless you are confident in where it will take you. Phishing emails may include links to the both the legitimate company’s real site as well as links that will take you to a fraudulent version of the site. Often the fraudulent links will be disguised by making slight changes to the correct URL, such as “www.amzon.com” or “z00m.us”. To avoid clicking on the fraudulent email link, you can always open a browser and log in to the actual site by manually entering the URL you’re familiar with.
- Enable DMARC. DMARC allows an organization to identify and block or quarantine potentially fraudulent emails sent or received by their domain. With DMARC enabled, companies can install Verified Mark Certificates (VMCs) to display their company logo next to the sender field in email clients so that users can be confident who the sender is—before they open the email.
Phishing emails will most likely continue to be a threat for the foreseeable future. But taking these simple precautions can keep youself and your customers from being a phishing victim.
This post was sponsored by our partners at DigiCert, the world’s leading certificate authority and SSL provider.
